Security overview - Azure Arc
Security gaps often emerge when managing infrastructure across public cloud, private cloud, and on-prem environments. Azure Arc helps bridge those gaps by extending Azure security tools to Arc-enabled servers running anywhere. Read this Microsoft Learn article to see how it works and how your organization can benefit. Contact Aavex Technology Corporation for a complimentary security assessment of your hybrid environment.
What is the shared responsibility model for Azure Arc-enabled servers?
The security of Azure Arc-enabled servers is a shared responsibility. Microsoft is responsible for securing the cloud service that stores system metadata, protecting privacy, documenting optional security features, publishing regular agent updates, managing RBAC access, and securing the server infrastructure. Users are responsible for securing the server itself, managing credentials, determining the application of security features, and ensuring compliance with legal and internal policies.
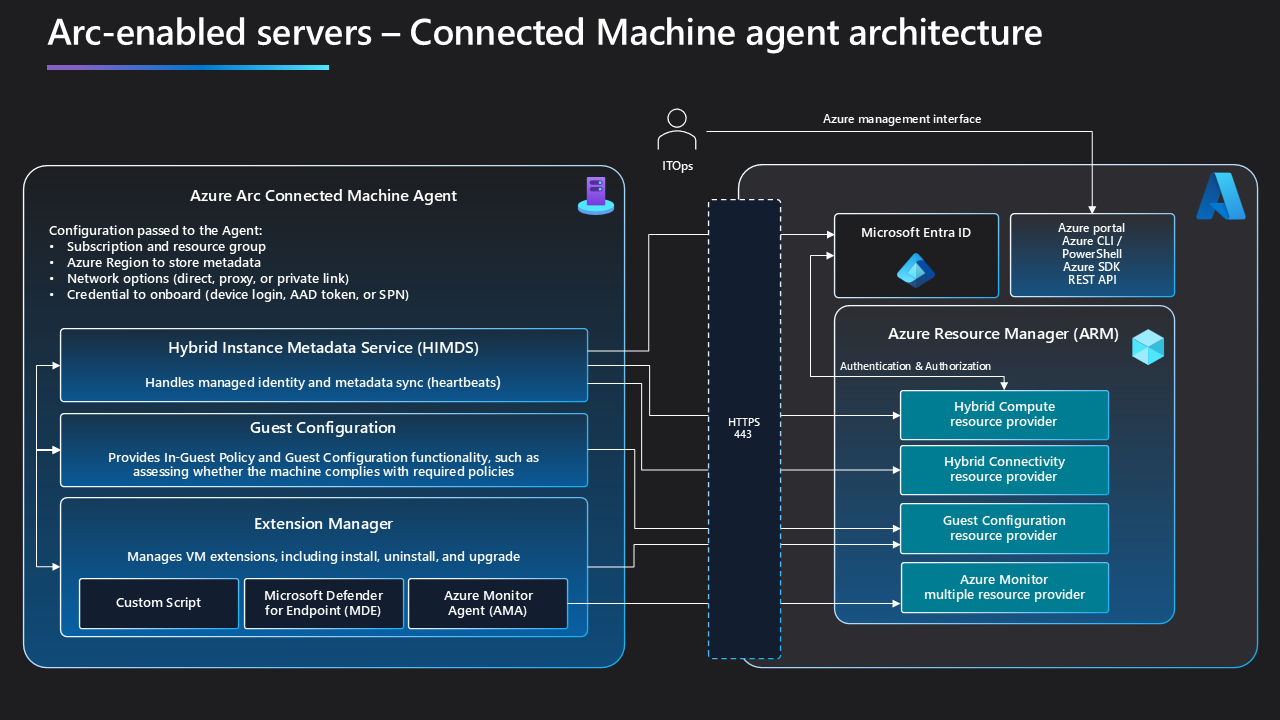
How does the Azure Connected Machine agent function?
The Azure Connected Machine agent acts as an enablement platform that connects your machine to Azure. It establishes a relationship with your Azure subscription, provides a managed identity for authentication, enables additional capabilities through extensions, and enforces settings on your server. The agent is essential for relaying data and actions between your managed server and Azure.
What security measures should be taken for Tier 0 assets?
For Tier 0 assets, it is recommended to use a dedicated Azure subscription to minimize access and closely monitor permissions. You should also disable unnecessary management features, such as remote access capabilities and the extension manager, unless they are needed. Implementing an extension allowlist can help restrict the use of extensions to only those that meet your security requirements.
Security overview - Azure Arc
published by Aavex Technology Corporation
Aavex Technology Corporation has been a leading Managed Security and Service Provider since 2002.
Business First • Security Focused• Effortless IT
We take a business first, security focused approach to providing our IT services. Aavex Technology Corporation specializes in wide range of services, including tailored IT services, hardware procurement, Cloud migration services, employee on-boarding and off-boarding checklists, network and IT infrastructure monitoring, Voice over IP and solutions for small and medium businesses and their owners in the Chicagoland area. We are committed to providing each one of our clients the highest level of quality service and support. Our unique IT team is incredibly friendly and can help you every step of the way in growing your business.
Assess • Deploy • Manage
Our approach uses our expertise to assess your IT infrastructure as it relates to your data assets and compares it to standards and processes, we have in place. Our standards will produce recommendations that result in a stable environment. The outcome is data assets that are kept confidential, unchanged, and available to your organization when you need it. Our helpdesk and on-site services will deliver the excellent support when you need it.



